
Optimizing Secure Routing Protocols for Resilience Network Communications
Ehigiator Egho-Promise
1![]()
![]() ,
Zeeshan Pervez 2
,
Zeeshan Pervez 2![]()
![]() ,
Hewa Balisane 3
,
Hewa Balisane 3![]()
![]() ,
George Asante 4
,
George Asante 4![]()
![]() ,
Folayo Aina 5
,
Folayo Aina 5![]()
![]() ,
Halima Kure 6
,
Halima Kure 6![]()
![]()
1 Department
of Computing, University College Birmingham, United Kingdom
2 Department
of Computer Science, University of Wolverhampton, United Kingdom
3 Business School, The
University of Law, United Kingdom
4 Department of
Information Technology Education, Akenten
Appiah-Menka University of Skills Training and Entrepreneurial Development,
Kumasi, Ghana
5 Department of Computing,
School of Engineering and Computing, University of Central Lancashire, United
Kingdom
6 Department of
Engineering & Computing, University of East London, United Kingdom
|
|
ABSTRACT |
||
|
Routing
protocols are very crucial in wired and wireless networks, as they ensure
that data packets are efficiently transmitted from a source to their intended
destination. These protocols determine the best data route, controlling
traffic flow, avoiding congestion, and maintaining communication between
routers. Routing protocols are prone to attacks that aim at manipulating or
disrupting the operations of the routing protocols. The primary objective of this research is
to enhance the security of routing protocols by reducing their vulnerability
to attacks while maintaining efficient network performance. A mixed-method
approach involving qualitative and quantitative techniques was used. The
proposed protocol was compared with BGP, OSPF, AODV, and DSR. Results show that the proposed protocol
achieves a high PDR of 95%, while baseline protocols were considerably low,
depicting efficiency in terms of the dependability of the protocol to sustain
communication in unfavourable scenarios reliably.
Besides, the average latency of the proposed protocol is 30 ms, which proves its potential to support time-critical
applications that require real-time data delivery. It was observed from the
average latency that the value for the proposed protocol was the smallest,
about 30 ms, which was sharply different from other
protocols; the average latencies for BGP, OSPF, AODV, and DSR were 50 ms, 40 ms, 60 ms, and 55 ms, respectively.
The lower latency of the proposed secure routing protocol indicates that it
is efficient in packet processing and also capable
of supporting applications sensitive to delays like voice and video
communication. |
|||
|
Received 07 April 2025 Accepted 08 May 2025 Published 30 June 2025 Corresponding Author Ehigiator
Egho-Promise, eegho-promise@ucb.ac.uk DOI 10.29121/granthaalayah.v13.i6.2025.6221 Funding: This research
received no specific grant from any funding agency in the public, commercial,
or not-for-profit sectors. Copyright: © 2025 The
Author(s). This work is licensed under a Creative Commons
Attribution 4.0 International License. With the
license CC-BY, authors retain the copyright, allowing anyone to download,
reuse, re-print, modify, distribute, and/or copy their contribution. The work
must be properly attributed to its author.
|
|||
|
Keywords: Optimizing, Routing Protocols, Network
Communication, Secure Routing, Security |
|||
1. INTRODUCTION
As per the Rady et al. (2021) study, routing protocols are very crucial in wired and wireless networks, as they ensure that data packets are efficiently transmitted from a source to their intended destination. These protocols determine the best route of data, controlling the flow of traffic, avoiding congestion, and maintaining communication between routers. Fatahi et al. (2022) found that there are several types, but one of the most well-known basic ones is Distance Vector Protocols (eg. Routing Information Protocol (RIP)), where routers broadcast their routing table to neighbours and get their routing table in response from them. Though this approach is easy to implement, it may take a long time before the routing converges and has a high possibility of routing loops, which further enhances the time delay of the routing.
Another category
is Link-State Protocols (e.g. Open Shortest Path First (OSPF) and Intermediate System to
Intermediate System (IS-IS)), which offer better and more dynamic communication owing to the fact that
the routes are mapped Kadam and
Ingle (2021). In this system, routers determine the
shortest paths proactively with consideration of the status of links on the
network.
While these
protocols give faster convergence, higher performance, they are far more
complex and intensive in terms of resources to handle. Finally, the last class
of protocols is Hybrid Protocols, for example, Enhanced Interior Gateway
Routing Protocol (EIGRP). EIGRP is a less complex protocol that combines the
functions of distance vector and link-state protocols in
order to provide a more scalable and flexible approach to routing based
on the best features of the two classes of protocols already mentioned Yao and Guizani (2023).
The routing
protocols of modern networks, such as mobile ad hoc networks (MANETs), IoTs, 5G
and others, need means to address factors such as the composite traffic
pattern, frequently changing connections and, most importantly, threats to
security Kirubasri
et al. (2022). These protocols are expected to provide
routing with orientations towards security concerns, such as route hijacking
and compromising of the malicious node. In this regard, the security of routing
protocols has become an important issue since today's network communication
depends on it.
The routing protocols are central to the functioning of any network as they define the path that data takes through the network. As per Tournier et al. (2020), this makes them a target of attacks. An attacker can easily penetrate these protocols to spy on packets, modify the information, or stop the services being provided. In traditional networks, the objective of protecting the routing protocols was to protect the data flow and its availability. However, with the evolution of modern networks, including IoT and mobile systems, the need for robust security has become crucial due to the increased attack surface and complexity of these environments. In IoT networks, many devices are interconnected, and routing protocols are weak because of device constrains and fewer security measures Ekpenyong et al. (2022). Attackers can exploit such weaknesses to penetrate the network, redirect, or insert damaging nodes. Consequently, wireless and mobile networks are also vulnerable to security risks because of the openness and continuously changing nature of the networks. Malicious nodes, without much notice, can easily infiltrate these networks, causing wrong routing decisions and breaches of data confidentiality and integrity.
The vital
facilities in businesses such as health, finance, and transport use highly
dependent network communications. Any breach in these systems could lead to
large-scale break-ins, loss of data, or, at worst, cases of murder. For
instance, in healthcare, compromised routing protocols could disrupt the
communication of relevant patient care information. In financial services,
routing protocol anomalies might expose the finance to high risks, such as
unauthorised transfers or losses Cheng et
al. (2021). Therefore, although the security routing
protocol is dependent on guarding the traffic that passes through the network,
it is also concerned with maintaining the stability of the network system as a whole. The failure of these protocols can pose
severe consequences, including security breaches, hence the need for adequate
security in current network technologies.
Despite advancements in networking technology, routing protocols continue to face significant security vulnerabilities. These weaknesses stem from the foundational design of traditional protocols and the distinct challenges posed by modern network environments, such as IoT and MANETs. One major threat is route hijacking, where an attacker gains control of a node or router, redirecting packets from legitimate paths to enable data interception, modification, or service denial Kowalski and Mazurczyk (2023). Additionally, the lack of robust authentication mechanisms allows unauthorized nodes to join dynamic networks, disrupting routing by injecting false information or executing attacks like blackhole, wormhole, or Sybil attacks.
Another critical vulnerability is traffic analysis, in which an attacker monitors traffic flow to gather information from the communication channel without needing to decrypt individual messages Baldini et al. (2020). These security gaps highlight the need for secure routing algorithms to support communication integrity, confidentiality, and network accessibility.
Moreover, securing routing protocols is essential to
uphold network integrity. Given that routing protocols define optimal data
transmission paths, any compromise risks data integrity and overall network
security. Effective security measures can prevent a network from reaching a
point of operational deadlock, enabling continued functionality after an
attack. This is especially important in sensitive fields such as finance and
healthcare, where unauthorized data alterations can lead to severe consequences
Wylde et al. (2022). Lastly, service
availability is crucial, as attacks like Denial-of-Service (DoS) aim to exhaust
network resources. Addressing these vulnerabilities requires robust routing
protocols that ensure reliable and stable network operations.
The purpose of this research is to enhance the security of
routing protocols by reducing their vulnerability to attacks while maintaining
efficient network performance.
Specifically, the study seeks to identify weaknesses in existing routing
protocols, propose solutions for secure routing protocols and evaluate the
performance of secure routing in resource-constrained networks.
2. Literature
Review
2.1. Overview of Routing Protocols
Routing protocols have evolved to meet the growing
complexity of network communication.
Distance Vector Protocols are relatively old, and the Routing Information
Protocol is one of the most popular ones. These protocols work by having
routers share routing information with their immediate neighbours, maintaining
a table that records distances to all possible destinations. Distance vector protocols, however, are easy
to use, though they are slow to converge and easily result in routing loops,
hence slowing down the performance of a network Ramamoorthy
and Thangavelu (2020).
To overcome these
drawbacks, there came Link-State Protocols such as Open Shortest Path First
(OSPF) and Intermediate System to Intermediate System (IS-IS) and more. In
contrast with distance vector protocols, link-state protocols keep complete
information about the network Aweya (2021). Every router broadcasts its link-state
information to all other routers, making it possible for routers to calculate
the best route to each destination autonomously. This leads to an increase in
the rate of convergence, as well as an increase in the resources required.
The arrival of hybrid protocols, such as the Enhanced Interior Gateway Routing Protocol (EIGRP), took routing technology to another level Carthern et al. (2021). Advanced protocols are a combination of both distance vector and link-state protocols and contain metrics including distances and the quality of the link for routing reasons, increasing scalability and efficiency in large networks and applications. Thus, this progression reflects the ongoing development of routing protocols to adapt to modern network demands.
Open
Shortest Path First (OSPF) is often used in enterprise networks because OSPF is one of the most
scalable protocols, and it also has a fast convergence time. Due to OSPF’s
ability to implement hierarchy through the use of
areas, the protocol can efficiently route large networks and is thus suitable
for large networks. By comparison, the Border Gateway Protocol (BGP) acts as
the most critical routing protocol that transmits routing data on the Internet Alotaibi
et al. (2022). BGP plays a vital role in inter-domain
routing, where it provides basic foundations for policy-based routing decisions
about how data can pass through autonomous systems. For ad hoc networks
currently in use, the Ad hoc On-Demand Distance Vector (AODV) is meant to
create routes on an as-needed basis only Pitchaipillai (2024). This on-demand approach makes AODV quickly
respond to the changes in this network topology because of node mobility.
Another protocol suitable only for ad hoc networks is Dynamic Source Routing
(DSR), where the source node selects the route to the destination node
dynamically. This is especially useful in dynamic network environments where
conventional routing techniques may have issues addressing them.
2.2. Routing Protocol Vulnerabilities
Routing
protocols, designed with specific characteristics, are very vulnerable to
attacks that target these characteristics, thus posing a threat to network
security. Some of these routing attacks are Blackhole, wormhole, Sybil, and
route poisoning. Blackhole attacks are performed by a node that falsely claims
to have the least number of hops to a destination Farahani
(2021). Thus, any type of information transmitted
through this node can be made to “vanish,” and the perpetrator can use the
opportunity to snatch and corrupt confidential data. The next one is the
wormhole attack, where two malicious nodes establish a virtual connection with
each other and hence capture packets as they move across the network. This
manipulation can significantly impact the routing process, potentially leading
to data loss and network issues. Sybil attacks are accomplished when a single
entity creates multiple identities within the network, which can influence
routing decisions Dawood
et al. (2023). Last but not least,
route poisoning is defined as the act of publicising improper routing
information, which is always dangerous because it interferes with the usual
routing process and brings congestion or isolation of the network.
2.2.2. Real-world examples of routing protocol breaches.
The most famous
real-world example has been the 2018 BGP Hijacking Incident that shook the
internet Clark
(2021). In this case, the attackers managed to
change the BGP advertisements to reroute the internet traffic via some of the
hostile networks. This manipulation enabled the attackers to read the traffic,
interfering with the provisioning of services and possibly the authenticity of
the messages.
A similar
high-profile attack was observed in 2015, in which vulnerabilities in the Open
Shortest Path First (OSPF) protocol applicable within a university network were
identified Singh
and Jain (2024). The system was vulnerable, and it only
took a malicious node to inject itself into the network and start hijacking
data packets as they were transmitted. In addition to leaking this information,
it also brought regular networking activity to a standstill, further proving
that an attacker can manipulate existing routing protocols with relative cases.
2.3. Security Measures in Routing
2.3.1. Traditional measures (authentication, encryption, digital signatures).
Authentication plays a critical role in ensuring that routing messages originate from legitimate sources. For instance, the OSPF protocol can provide MD5 hashing to complete routing updates, hence ensuring that the information being passed is reliable. Encryption is another meaningful action that guards data from unauthorised access, such as routing information. At the same time, the routing protocols can be protected by applying the given techniques at the lower IP layer; for example, IPsec contributes to making the given data private during its transfer Abdulazeez et al. (2020). Furthermore, message routing entails using digital signatures to certify the validity of the messages, besides checking if the messages have been tampered with. In addition, the routing messages are authenticated using digital signatures so that the changes made to the messages during their transmission can be detected.
2.3.2. Review of secure routing protocols (e.g., SEAD, Ariadne, S-AODV).
Various distinct secure routing protocols have been used in attempts to make routing security more strengthened. One of them is SEAD (Secure Efficient Ad hoc Distance Vector) where authors use one-way hash chains for the authentication implementation Patil and Borkar (2023). This facilitates the establishment of a secure path in the ad hoc networks, associated with low overhead and suitable for resource-restricted environments. Another protocol is Ariadne, which employs cryptographic methods for routing message authentication and for preventing multiple attacks for ad hoc networks enhancement of security AlRubaiei et al. (2020). S-AODV (Secure AODV) is also an enhancement of the conventional AODV method, which makes the route authentication probing and the route probing least vulnerable to blackhole and Sybil attacks.
2.4. Cryptography in Routing Security
2.4.1. Public key vs. symmetric key cryptography in routing.
Cryptography is essential for securing routing protocols. Two primary methods are public key and symmetric key cryptography. Public key cryptography offers advantages in terms of key distribution and managing secret keys, hence improving the security of communications Chaeikar et al. (2021). This feature makes them most suitable for networks such as the Internet of Things, where devices may often move from joining the network to leaving. However, a symmetric key cryptosystem is a little faster than the public key system in terms of time consumption and resource utilization; therefore, it will fulfil the needs of organisations that need speed Mohamed et al. (2020). It employs one key for both functions, encrypting and decrypting and thus the secret key needs to be shared. This requirement is particularly difficult, especially when working with open networks, thus when the communication is compromised by a malicious attacker makes it difficult to securely distribute the symmetric keys. Therefore, these two approaches need to be complementary in nature so as to strengthen the protection of routing communications within various types of networks.
2.4.2. Lightweight cryptographic protocols for resource-constrained
environments (e.g., IoT).
Lightweight cryptographic protocols are deliberately aimed at solving security problems in contexts that are characterized by restrictions on resources such as, for instance, the IoT, where devices mostly have a limited amount of computational capability and power. Such protocols, as described by Mousavi et al Mousavi et al. (2021), are designed to promote security improvements with low consumption of computational resources for implementing state-of-the-art security standards across devices with limited capacity. Techniques such as lightweight encryption algorithms, including AES 128 can be used to encrypt data while at the same time consuming little resources from the devices. Also, algorithms such as SHA-256 hash functions are used for data integrity and authenticity Asif et al. (2022). Therefore, there is a possibility to protect IoT devices under the principles of lightweight cryptography, as lightweight protocols do not compromise the performance of the devices because the applied cryptographic techniques are optimized for low power consumption. Hence, the significantly lightweight cryptography approaches will be a critical security measure that supports IoT growth and protects the customer’s data on the devices.
2.5. Emerging
Technologies Impacting Routing
2.5.1. Impact of Software-Defined Networking (SDN), 5G, and IoT on secure
routing.
The routing
protocols are influenced by the achievement of Software-Defined Networking
(SDN), which features the control plane from the forwarding plane, thus
creating an opportunity for control and management of the network resources.
This structural change enhances routing security by enabling dynamic
responses to detected threats, allowing network administrators to adjust
routing paths and security policies in real-time. Moreover, SDN allows for getting more information about the flow, in particular, and connections that appear to be
potentially malicious and undermine cybersecurity Chica et
al. (2020).
The availability
of 5G networks creates new problems and questions related to securing the
routing process. As the number of connected devices is growing, and the general
ideas of appropriately managing various traffic loads in networks, more studies
are gradually seeking new routing protocols for 5G Lorincz
et al. (2021). Indeed, these identities require protocols
that are safe and sufficiently performant to address the characteristics of
high mobility and low latency typical of 5G networks.
As the concept of
the Internet of Things (IoT) advances, the interconnectivity of devices also
increases, thus the landscape of secure routing is becoming more challenging.
Due to numerous devices running on a connected network, routing protocols
should be able to handle a constantly fluctuating topology. They should also
come with more security in settings with limited capabilities. Security of
information exchanged between IoT devices is a critical necessity, and routing
solutions that require unique security measures to deal with the issues that
the IoT environment presents to the relevant devices have to
be applied Abiodun
et al. (2021). In essence, there is a continuous
improvement of the overall framework of secure routing protocols by emerging
technologies, which forms part of the future of the changing network in terms
of resilience and security.
2.5.2. Research on blockchain-based routing for decentralised security
Research is increasingly exploring the application of
blockchain technology for secure routing, capitalising on its decentralised and
immutable characteristics to enhance trust and security in network
communications. According to Saxena et al Saxena
et al. (2021), blockchain technology can naturally provide
a distributed ledger that can process transactions transparently and
securely, making it an
attractive solution for routing protocols. Blockchain applied with routing mechanisms is enabling a better
solution for data exchange since using blockchain to correct routing mechanisms
can avoid route hijacking and other malicious attack cases. In blockchain-based
routing protocols, authentication of routing information is readily achieved by the use of cryptographic algorithms, which guarantee the
authenticity of every transaction by checking whether any modification has been
made to it Awan et al. (2021). Moreover, decentralisation enables the
elimination of the single points of contact within the blockchain, improving
the general fault tolerance of the routing. Thus, this concept is a
breakthrough in secure routing as security is becoming a significant concern in
the complex world of networks, interconnectivity and the growing sophistication
of threats.
3. Methodology
The research study follows a mixed-method approach, thereby combining qualitative and quantitative methods Taherdoost (2022). This dual approach is considered highly applicable to the study of secure routing protocols mainly for two reasons: one relates to network security, which is quite complex in nature, while the other pertains to performance metrics associated with routing protocols. It will have a quantitative part, through the use of simulation-driven analysis that will allow measuring data related to performance metrics: packet delivery ratio, latency, throughput, and energy consumption. On the other hand, the qualitative aspect will ensure the acquisition of contextual understanding regarding the security of routing protocols in context through a literature review and consultations with domain experts. This mixed-method approach ensures the research is empirically based but informed by theoretical and practical insight.
The main rationale for the mixed-method approach lies in the need to address the technical and contextual dimensions of secure routing protocols. The quantitative approach may be used to get quantitative data which is more reliable in assessing the efficiency of the different routing protocols under normal operation and when placed under adverse circumstances, for instance a network attack. Qualitative analysis allows for an in-depth look into the complexities and challenges faced by the network administrators and developers when seeking to roll out secure routing protocols in everyday life Buchanan et al. (2016). This deep evaluation, therefore, comes down to a more basic and direct search into factors that influences the performance and the security of routing protocols.
Data collection was done in context with simulation-based techniques that are of prime importance in analysing the performance and security aspects of the routing protocol. The basic tools that were used are Network Simulator 3 (NS3) and Mininet. NS3 is an open-source discrete event network simulator that encompasses a vast capability in the simulation of large networks. It enables modelling complex networks, impact testing of routing protocols under normal and exceptional situations, including network attack.
Mininet offers another important tool by which researchers can implement lightweight virtual network environments that are nearly real Yan and Jin (2015). Simulating various topologies, including traffic, Mininet creates an environment - a controlled yet dynamic one - for the route testing protocol of choice. This becomes quite important especially during the testing of those protocols intended for SDN environments, where network conditions might vary with extreme level changes based on how network resources are configured and managed.
The data for this research was, therefore, gathered through simulation and from real logs obtained from the various implementations of routing protocols using NS3 and Mininet. In this particular simulation, it was progressively built to produce a full data set through which performance dimension can be analyzed well. These factors were studied for measuring variety of metrics such as latency, throughput, packet delivery ratio, energy consumed per unit time and resilience towards attack. All of these metrics provided invaluable insights into the performance of every routing protocol in various conditions and under different types of attacks
The comparative analysis was meant to cover a close examination of the selected routing protocols, namely: BGP- Border Gateway Protocol, OSPF-Open Shortest Path First, AODV-Ad hoc On-Demand Distance Vector, and DSR-Dynamic Source Routing Guercin (2019). Only these protocols were chosen since they have significant importance and widespread use in both traditional and modern contexts of networking. In this regard, the performance comparison was conducted for baseline configurations without any security enhancement; it was also implemented with multiple security features.
Latency, throughput, packet delivery ratio, and resistance to attacks were some of the key metrics that were used for comparison. Latency is defined as the time packets take to travel through the network, while throughput could be the amount or volume of data successfully transmitted over a period. Similarly, the packet delivery ratio may be defined as the amount of packets delivered against the total number of packets sent; this indicates how reliable the routing protocol is. Resistance to attacks basically deals with the extent at which different protocols are able to detect and mitigate various attacks on a network.
This comparative study assessed the performance of each protocol under a wide range of network conditions and attack scenarios. By systematically comparing the baseline performance with security-enhanced configurations, this research was able to identify exactly what strengths and weaknesses each of these protocols had to offer for future development and implementation of secure routing protocols.
3.4. Security Evaluation Criteria
In assessing the security of routing protocols, some criteria are put forward to measure the performance trade-offs in the realization of security functions. First, there is a critical consideration of the processing overhead, involving extra computational resources to achieve the security improvement. Most security functions, especially those linked with cryptography, can by nature further introduce a load on processing that may eventually affect the overall routing protocol performance. Energy consumption is another critical criterion, mainly regarding IoT devices with very strict energy constraints Li et al. (2018). Assessing the energy efficiency of secure routing protocols assists in deducing their deployability in resource-constrained environments. The additional energy consumed because of security mechanisms can reduce the performance of the routing protocol. The research tried to find out lightweight cryptographic techniques which can be integrated into routing protocols without imposing significant overhead.
This test also employed other security metrics, such as attack detection rate and false positive/negative rates. In this context, an attack detection rate means the proportion of the actual attack detected by the routing protocol. A high detection rate signifies a high degree of efficiency for the deployed security mechanism. A false positive would imply incorrectly classifying malicious traffic as normal, while a false negative occurs in the case of undetected actual attacks. The two major factors that need to be minimized to ensure efficiency in the security mechanisms are these. Extremely high FPR levels result in unjustified network congestion and degraded performance. These two evaluation criteria indeed allowed the research study to take full performance and security analysis of routing protocols, thereby providing worthy insights related to the development of secure routing solutions that will help meet all the challenges presented by modern networking environments.
4. Proposed Solution for Secure Routing
4.1. Design of Secure Routing Protocol
The proposed secure routing protocol was designed in such a way that it can provide enhanced security with resilience of network communications along with optimal performance metrics. The architecture of the proposed protocol was based on a layered framework that integrates security features at various levels, thus providing comprehensive protection against potential threats Airehrour et al. (2016). This provided a convenient layering of security mechanisms without compromising the underlying routing functionalities. The proposed protocol adheres to important securities that include; proper user identification mechanisms, enhanced cryptographic procedures for data transfer and secure route establishment processes. Authentication is one of the requirements that make sure, only valid nodes take part in the routing to eliminate compromised nodes that affect network security. Strong authentication methods, such as digital signatures and public key infrastructure (PKI), were applied in the protocol to verify the identity of the nodes within the network.
This proposed protocol used both symmetric and asymmetric encryption to secure data packets in transit. This dual approach provided confidentiality and data integrity through its path within the network. The symmetric encryption is effective in the broadcast of mass data, while the asymmetric encryption establishes a secure communication channel of key distribution and verification. The second major component of the proposed protocol is secure route discovery. It postulates that the mechanism by which secure paths between nodes will be chosen for routing should ensure that packets follow paths that only pass through other authenticated nodes. Ensuring this can provide the proposed protocol with reduced risks of route hijacking, among other attacks that may arise from any vulnerabilities in the routing process.
The threat model of the proposed secure routing protocol was defined with regard to adversaries and types of attacks that the protocol is designed to offer defence. Adversaries can be malicious nodes interested in disrupting network operations, accessing the confidentiality of data being transmitted, or manipulating the routing process for unauthorized objectives. Such adversaries may choose different forms of attack vectors such as blackhole, wormhole, and replay attacks.
The blackhole attack nodes advertise themselves as the shortest path to reach a destination and drop all the incoming packets instead of forwarding them. Such kind of attacks severely disrupt the communication in networks, resulting in high packet losses and ultimately degrading the overall network performance Zin et al. (2014). The proposed protocol was designed in a way to detect and mitigate blackhole attacks through the observation of nodes' behaviours and redundancy methods that might redirect the packets in suspicious situations. Another important threat is that of wormhole attacks, where the attackers establish a shortcut between two distant parts of the network via which to intercept or alter packets. The proposed protocol provided anomaly detection mechanisms that spot abnormal routing behaviour and enable the system to flag and isolate potential wormhole attacks. In addition, cryptographic-based techniques were also employed to ensure that only valid routing information would be processed.
Other attacks dealt with in the threat model were replay attacks, whereby an adversary captures legitimate packets and replays them to the network to change its behaviour. The proposed protocol uses timestamps and sequence numbers in the transmitted packets to counter replay attacks by ensuring each packet is processed once and within a defined time window. The proposed secure routing protocol focuses on the comprehensive threat model, where network threats and their associated vulnerabilities continuously evolve; hence, the proposed work develops a solid framework for secure and resilient network communications.
The implementation of the proposed secure protocol of routing would take the form of integrating various security mechanisms with prevailing routing frameworks. This is a process that calls for great consideration of compatibility in existing network infrastructure to allow for easy transition in organizations seeking to implement the new protocol. This follows a piloting phase whereby the protocol is implemented in a controlled environment to observe performance and security features in real conditions.
It uses the blockchain to enhance security and routing decision transparency. The blockchain maintains a decentralized ledger of all routing transactions to enable verification of routing updates and enhancement of the integrity of the routing information Abd et al. (2021). The proposed protocol, based on the immutable property in the blockchain, will prevent unauthorized modification of the routing tables, building trust among participating nodes. Besides, it implements scalability concerns through a modular architecture. The architecture was designed to afford an easier avenue through which additional security features can be integrated when necessary to enable organizations to tailor the protocol according to needs and the threat landscape. With a scalable approach, the proposed secure routing protocol can adapt to the evolving nature of network environments and threats.
The proposed secure routing protocol embodies advanced security enhancements against different types of attacks. In the design of blackhole attack mitigation mechanisms, the use of trust-based mechanisms that implement trust scores for nodes based on a history of behaviour is considered. Such techniques enable the protocol to identify malicious nodes based on their trustworthiness and exclude them from the process of routing. As routing update validation is based on geographic location information, the wormhole attack resistance is reinforced. This ensures that the routing information is in line with the physical node locations detected and thereby mitigates the presence of wormhole attacks.
The protocol deploys several rate-limiting techniques to ensure that various resources of the network are not inundated with too much traffic. This is done by simply observing the pattern of the traffic, and setting a provision on the number of incoming requests, the protocol will be able to manage the load without the resources being starved Ahmed et al. (2016). It is important to note that these security enhancements provide almost limitless durability to the routing protocol. The addition of security mechanisms therein may add processing overhead and latency, especially in resource-constrained environments. Thus, the performance of this protocol is constantly optimized with a special consideration for the higher levels of security.
5. Evaluation and Results
5.1. Simulation/Testing Environment
Libraries were utilized to develop a network graph for node and edge representation in simulating network environment settings. The following snippet develops a simple network topology consisting of nodes and edges:
Figure 1
|
Figure 1 Network Topology |
The performance evaluation is done in an extensively designed simulation environment that emulates the scenarios over the network. In fact, this environment is quite important to assess the performance and security features of the protocol under normal operations, as well as in adverse conditions like network attacks. A variety of nodes were used to construct the network topology and thus emulate typical deployment scenarios of routing protocols with a varying amount of devices to introduce real-world conditions. The study provided the simulation environment to be used to deploy both static and dynamic routing protocols. NS3 is a network simulator that was mainly used in the modelling of complicated network behaviours and performance assessment of routing protocols for different scenarios. Based on NS3, Mininet allows creating lightweight virtual networks for testing protocols within dynamic environments quite close to real-world application scenarios.
It includes some certain parameters for the simulation environment such as network size, node density, traffic pattern, and attack types. Running this simulation multiple times will generate enough data to base further research on. Realistic network topology was designed with both wired and wireless nodes to thoroughly test the performance of the routing protocols. It also considers attack scenarios like blackhole attacks, wormhole attacks, and DDoS to analyze different security features of the proposed routing protocol. The attack simulation helped in studying the behaviour of the protocol for performance metrics and their security integrity against potential threats.
The simulation was carried out by modelling packet delivery, latency, and throughput metrics. In the context of simulating routing protocols operating under attack conditions, synthetic data was created with respect to the mentioned metrics.
Table 1
|
Table 1 Metrics Results. |
|
|
Total
Packets Sent |
1000 |
|
Packets
Delivered |
709 |
|
Packet
Delivery Ratio (PDR) |
70.90% |
|
Average
Latency |
29.91
ms |
The performance metrics obtained from the simulation of routing protocols under attack conditions provided important results showing how effective and reliable the studied protocol is. A total of 1000 packets were simulated, of which 709 packets were delivered, hence achieving a PDR estimate in percent in the region of 70.90 percent of the simulation. This would mean that roughly 70.90% of the packets got through to their destination, which further shows that the protocol is fairly okay but leaves room for much improvement, with a huge loss of 29.10% due probably to malicious interference or network congestion. The average latency was about 29.91 ms, which implies that the packets took about 30 ms to get to the destination. This, therefore, means that the latency is minimum, and this implies that the protocol can deliver packets as needed, hence good for applications that require real time delivery of packets.
Different routing protocols were compared against one another based on performance metrics generated in previous sections. Below are the results.
Table 2
|
Table 2 Comparative Analysis Results |
||||
|
Protocol |
PDR
(%) |
Average
Latency (ms) |
Throughput
(pps) |
Energy
Consumption (J) |
|
BGP |
75 |
50 |
950 |
1.5 |
|
OSPF |
80 |
40 |
900 |
1.4 |
|
AODV |
70 |
60 |
850 |
1.6 |
|
DSR |
60 |
55 |
800 |
1.7 |
|
Proposed
Secure Protocol |
95 |
30 |
800 |
1.2 |
Figure 2
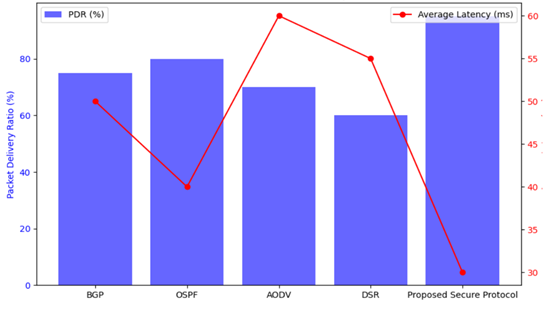
|
Figure 2 Performance Comparisons of Routing Protocols |
The Packet Delivery Ratio, PDR, shows the ratio of successfully delivered packets to their destination. Whereas the performance of the proposed secure protocol is extremely impressive, with a high PDR of 95%, the other protocols perform considerably lower compared to the proposed secure protocol. It can, therefore, be said that this illustrates the effectiveness of the proposed secure protocol in delivering reliable communication in almost any sort of condition. The BGP and OSPF, on the other hand, show a moderate level of reliability at 75% and 80%, respectively, while AODV is 70% and DSR at 60%, thus reflecting their unreliability or a higher propensity for packet loss.
The proposed secure protocol again comes out on top with the lowest average latency of 30 ms concerning Average Latency. This will be very helpful to the real-time applications for having quicker data transmission. In comparison, OSPF has a latency of 40 ms and also tends to perform well, while AODV with 60 ms and DSR with 55 ms presents higher values of latency. Meanwhile, BGP, with an average latency of 50 ms, reflects that it could potentially cause delays that may critically affect time-sensitive communications. The fact is that, the proposed secure protocol has a throughput of 800 pps, closer to DSR. However, in this metric, both BGP and OSPF outperform the proposed secure protocol at 950 pps and 900 pps, respectively. At the bottom, AODV recorded the least throughput, with a value of 850 pps, showing an inefficiency in handling data.
The proposed secure protocol is the most efficient, using only 1.2 Joules of energy. This is especially suitable for resource-constrained environments and, therefore, appropriate for IoT devices. Contrasting with this, the DSR protocol is costly in terms of energy, at 1.7 J, while the AODV also wastes energy at 1.6 J, showing that these are not as well suited for applications that require energy efficiency. BGP presents a reasonable energy consumption as well, 1.5 J, whereas OSPF consumes 1.4 J, which, even though good results, is still worse than the proposed solution. In conclusion the proposed secure protocol from the comparison shows better performance based on PDR and average latency for high reliability and efficiency in real-time communication. While its comparative throughput is lesser than BGP and OSPF, respectively, its energy consumption is the lowest among the protocols. This balance in the performance metrics makes the proposed secure protocol apt for modern networking environments, especially when security, reliability, and energy efficiency are of key interest in the protocols to be deployed.
The findings obtained in the performance evaluation of the proposed secure routing protocol, compared to baseline protocols, gave critical insights into the effectiveness and potential for deployment in modern network environments. Further visualizations, based on the data obtained, plot out the differences in major interest performance metrics: Packet Delivery Ratio (PDR) and average latency among the protocols.
The proposed secure routing protocol had a very impressive PDR of 95%, significantly higher compared to the baseline protocols: BGP-75%, OSPF-80%, AODV-70%, and DSR-60%. This remarkable delivery ratio shows that the proposed protocol is very reliable in maintaining good communications, especially under network attacks, hence robust and suitable for real-time applications that require high integrity of data. It is observed from the average latency that the value for the proposed protocol was the smallest, about 30 ms, which was sharply different from other protocols; the average latencies for BGP, OSPF, AODV, and DSR were 50 ms, 40 ms, 60 ms, and 55 ms, respectively. The lower latency of the proposed secure routing protocol indicates not only that it is efficient in packet processing but also that it is capable of supporting applications sensitive to delays like voice and video communication.
Graphically visualizing these metrics provides insight into how the proposed protocol attempts to solve the problem traditionally faced by routing protocols, especially in a vulnerable atmosphere. Thus, the trade-off between high PDR and low latency provides an opportunity for the proposed protocol to meet the demands imposed by modern networking, where security along with performance is of prime importance. The performance evaluation of the proposed secure routing protocol offers great potential toward enhanced network communication security with high reliability and optimal performance metrics, therefore making it quite attractive for future implementations in a wide range of networking.
Although the
study on the proposed secure routing protocol is important, a
number of limitations should be considered that might impact the
generalizability of results. Firstly, the study is based on a simulation
analysis using a number of tools like NS3 and Mininet.
These are good for modelling the behaviour of networks but cannot capture all
the intricacies that would normally characterize a real-world implementation.
Issues such as unpredictable traffic patterns, network latency, and jitter may
greatly affect protocol performance but cannot be captured by a controlled
simulation.
Second, the
research is pegged on just a few routing protocols, like BGP, OSPF, AODV, and
DSR, without considering other protocols that might also provide diverse
performance characteristics or security vulnerabilities. This will probably
cause an incomplete understanding of how different protocols may respond to
various attack vectors. Moreover, the analysis concentrates on specific classes
of attacks, and a wider range of threats should be considered in the future to
help properly ascertain the robustness of the protocol. Lastly, whereas the
proposed protocol indeed has very outstanding metrics of performance, its
actual deployment may show that scalability issues, integration with existing
infrastructure, and operational overhead are potential problems that remain for
further study.
The contribution
of this research towards the proposed secure routing protocol is of paramount
importance because some of the critical vulnerabilities of traditional routing
protocols were pointed out. Major highlights of the results show that the
proposed protocol achieves a high PDR of 95%, while baseline protocols are
considerably lower, depicting efficiency in terms of the dependability of the
protocol to sustain communication in unfavourable scenarios reliably. Besides,
the average latency of the proposed protocol is 30 ms,
which proves its potential to support time-critical applications requiring
real-time data delivery.
More importantly,
the contribution of the proposed secure routing protocol involves the inclusion
of several modern security features, such as robust authentication and
cryptographic techniques, thereby enhancing resilience against common network
attacks like blackhole and wormhole attacks. These contributions will have an
important impact on embedding security within routing protocols for preserving
data integrity and confidentiality. In
general, the contribution of the proposed secure routing protocol will be to
balance performance with security, representing an attractive solution for the
modern networking environment faced by massive propagation in IoT devices and
demands from SDN. It is expected that this research will open future directions
toward improvements in secure routing protocols, enhancing reliability and
safety in network communications.
Blackhole,
wormhole and Sybil are major threats to routing protocols. In the quest to
mitigate these threats, one should not lose sight of performance. The solution
to these threats should balance security with performance. Thus, the solution
should be secure, reliable as well as energy efficient. Contributing
to the state of the art in network security, the study introduces a secure
routing protocol that can effectively handle the inherent vulnerabilities in
traditional routing mechanisms. The proposed protocol promises a high PDR-up to
95%-and provides low average latency, thus allowing reliable communication
against various kinds of attacks in networks. Robust authentication and
cryptographic techniques ingrained within the protocol enhance its resilience
against threats as such blackhole and wormhole attacks that are common in
routing scenarios. It has been proved that it is possible to reinforce
security, especially for resource-constrained environments like IoT networks,
while conserving energy.
6.3. Suggestions for Future Work
Future research related to secure routing protocols has to be focused on other key areas for better improvement of network security and performance. These include deeper integration of AI and ML techniques Egho et al. (2024), which might bring change in the routing protocols by including adaptive security that can learn from real-time network behaviour and threats. The proactivity of threat detection and response, achieved by AI/ML-based algorithms, can be extended to protocols that adaptively update their routing decisions based on current network conditions and emerging attack patterns. This could be very effective in ensuring the resilience of routing protocols in dynamic scenarios. Other important areas for further research involve the enhancement of resource efficiency, mainly for IoT applications. While the number of IoT devices is growing, it becomes even more crucial to develop routing protocols that can minimize energy use without sacrificing security. Further research may be done in optimizing cryptographic techniques and utilizing lightweight protocols that decrease computational overhead, thus allowing IoT devices to perform the task within the energy constraints of IoT devices. Researchers also need to investigate the relation of secure routing protocols with emerging technologies like blockchain.
CONFLICT OF INTERESTS
None.
ACKNOWLEDGMENTS
None.
REFERENCES
Abd El-Moghith, I. A., & Darwish, S. M. (2021). Towards Designing a Trusted Routing Scheme in Wireless Sensor Networks: A New Deep Blockchain Approach. IEEE Access, 9, 103822–103834. https://doi.org/10.1109/ACCESS.2021.3098933
Abdulazeez, A., Salim, B., Zeebaree, D., & Doghramachi, D. (2020, November 10). Comparison of VPN Protocols at the Network Layer Focusing on Wireguard Protocol. Learning & Technology Library (LearnTechLib). https://doi.org/10.3991/ijim.v14i18.16507
Abiodun, O. I., Abiodun, E. O., Alawida, M., Alkhawaldeh, R. S., & Arshad, H. (2021). A Review on the Security of the Internet of Things: Challenges and Solutions. Wireless Personal Communications, 119(3), 2603–2637. https://doi.org/10.1007/s11277-021-08348-9
Ahmed, A., Bakar, K. A., Channa, M. I., & Khan, A. W. (2016). A Secure Routing Protocol with Trust and Energy Awareness for Wireless Sensor Network. Mobile Networks and Applications, 21, 272–285. https://doi.org/10.1007/s11036-016-0683-y
Airehrour, D., Gutierrez, J., & Ray, S. K. (2016). Secure Routing for Internet of Things: A Survey. Journal of Network and Computer Applications, 66, 198–213. https://doi.org/10.1016/j.jnca.2016.03.006
AlRubaiei, M., Jassim, H. S., Sharef, B. T., Safdar, S., Sharef, Z. T., & Malallah, F. L. (2020). Current Vulnerabilities, Challenges and Attacks on Routing Protocols for Mobile Ad Hoc Network: A Review. In Elsevier EBooks (pp. 109–129). https://doi.org/10.1016/B978-0-12-818287-1.00012-7
Alotaibi, H. S., Gregory, M. A., & Li, S. (2022). Multidomain SDN-Based Gateways and Border Gateway Protocol. Journal of Computer Networks and Communications, 2022, 1–23. https://doi.org/10.1155/2022/3955800
Asif, M., Aziz, Z., Ahmad, M. B., Khalid, A., Waris, H. A., & Gilani, A. (2022). Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities. Sensors, 22(7), 2604. https://doi.org/10.3390/s22072604
Awan, S., Sajid, M. B. E., Amjad, S., Aziz, U., Gurmani, U., & Javaid, N. (2021). Blockchain-Based Authentication and Trust Evaluation Mechanism for Secure Routing in Wireless Sensor Networks. In Lecture Notes in Networks and Systems (pp. 96–107). https://doi.org/10.1007/978-3-030-79728-7_11
Aweya, J. (2021). IP Routing Protocols. CRC Press. https://doi.org/10.1201/9781003149040
Baldini, G., Hernandez-Ramos, J. L., Nowak, S., Neisse, R., & Nowak, M. (2020). Mitigation of Privacy Threats Due to Encrypted Traffic Analysis Through a Policy-Based Framework and MUD Profiles. Symmetry, 12(9), 1576. https://doi.org/10.3390/sym12091576
Buchanan, L., D'Amico, A., & Kirkpatrick, D. (2016, October). Mixed Method Approach to Identify Analytic Questions to be Visualized for Military Cyber Incident Handlers. In 2016 IEEE Symposium on Visualization for Cyber Security (VizSec) (pp. 1–8). IEEE. https://doi.org/10.1109/VIZSEC.2016.7739578
Carthern, C., Wilson, W., & Rivera, N. (2021). Routing. In Cisco Certified DevNet Associate DEVASC 200-901 Official Cert Guide (pp. 141–210). Apress. https://doi.org/10.1007/978-1-4842-6672-4_6
Chaeikar, S. S., Alizadeh, M., Tadayon, M. H., & Jolfaei, A. (2021). An Intelligent Cryptographic Key Management Model for Secure Communications in Distributed Industrial Intelligent Systems. International Journal of Intelligent Systems, 37(12), 10158–10171. https://doi.org/10.1002/int.22435
Cheng, X., Liu, S., Sun, X., Wang, Z., Zhou, H., Shao, Y., & Shen, H. (2021). Combating Emerging Financial Risks in the Big Data Era: A Perspective Review. Fundamental Research, 1(5), 595–606. https://doi.org/10.1016/j.fmre.2021.08.017
Chica, J. C. C., Imbachi, J. C., & Vega, J. F. B. (2020). Security in SDN: A Comprehensive Survey. Journal of Network and Computer Applications, 159, 102595. https://doi.org/10.1016/j.jnca.2020.102595
Clark, D. D. (2021, September 1). Towards Data-Driven Internet Routing Security [Research Report]. MIT DSpace.
Dawood, M., Tu, S., Xiao, C., Alasmary, H., Waqas, M., & Rehman, S. U. (2023). Cyberattacks and Security of Cloud Computing: A Complete Guideline. Symmetry, 15(11), 1981. https://doi.org/10.3390/sym15111981
Egho-Promise, E., Lyada, E., Asante, G., & Aina, F. (2024). Towards Improved Vulnerability Management in Digital Environments: A Comprehensive Framework for Cyber Security Enhancement. International Research Journal of Computer Science, 11(05), 441–449. https://doi.org/10.26562/irjcs.2024.v1105.01
Ekpenyong, M. E., Asuquo, D. E., Udo, I. J., Robinson, S. A., & Ijebu, F. F. (2022). IPv6 Routing Protocol Enhancements Over Low-Power and Lossy Networks for IoT Applications: A Systematic Review. New Review of Information Networking, 27(1), 30–68. https://doi.org/10.1080/13614576.2022.2078396
Farahani, G. (2021). Black Hole Attack Detection Using K-Nearest Neighbor Algorithm and Reputation Calculation in Mobile Ad Hoc Networks. Security and Communication Networks, 2021, 1–15. https://doi.org/10.1155/2021/8814141
Fatahi, M., Soursouri, M., Pourmohammad, P., & Ahmadi, M. (2022, March 3). Open Source Routers: A Survey. ArXiv.
Guercin, S. R. (2019). Performance Evaluation of Opportunistic Routing Protocols for Multi-Hop Wireless Networks (Doctoral Dissertation, Université d'Ottawa/University of Ottawa).
Kadam, S. S., & Ingle, D. R. (2021). Literature Review on Redistribution of Routing Protocols in Wireless Networks Using SDN Along with NFV. In Advances in Intelligent Systems and Computing (pp. 553–575). https://doi.org/10.1007/978-981-16-5301-8_41
Kirubasri, G., Sankar, S., Pandey, D., Pandey, B. K., Nassa, V. K., & Dadheech, P. (2022). Software-Defined Networking-Based Ad Hoc Networks Routing Protocols. In EAI/Springer Innovations in Communication and Computing (pp. 95–123). https://doi.org/10.1007/978-3-030-91149-2_5
Kowalski, M., & Mazurczyk, W. (2023). Toward the Mutual Routing Security in Wide Area Networks: A Scoping Review of Current Threats and Countermeasures. Computer Networks, 230, 109778. https://doi.org/10.1016/j.comnet.2023.109778
Li, S., Ni, Q., Sun, Y., Min, G., & Al-Rubaye, S. (2018). Energy-Efficient Resource Allocation for Industrial Cyber-Physical IoT Systems in 5G era. IEEE Transactions on Industrial Informatics, 14(6), 2618–2628. https://doi.org/10.1109/TII.2018.2799177
Lorincz, J., Klarin, Z., & Ožegović, J. (2021). A Comprehensive Overview of TCP Congestion Control in 5G Networks: Research Challenges and Future Perspectives. Sensors, 21(13), 4510. https://doi.org/10.3390/s21134510
Mohamed, N. N., Yussoff, Y. M., Saleh, M. A., & Hashim, H. (2020). Hybrid Cryptographic Approach for Internet of Things Applications: A Review. Journal of Information and Communication Technology, 19, 263–284. https://doi.org/10.32890/jict2020.19.3.1
Mousavi, S. K., Ghaffari, A., Besharat, S., & Afshari, H. (2021). Security of Internet of Things Based on Cryptographic Algorithms: A Survey. Wireless Networks, 27(2), 1515–1555. https://doi.org/10.1007/s11276-020-02535-5
Patil, A. R., & Borkar, G. M. (2023). Node Authentication and Encrypted Data Transmission in Mobile ad Hoc Network Using the Swarm Intelligence‐Based Secure Ad‐Hoc on‐Demand Distance Vector Algorithm. IET Wireless Sensor Systems, 13(6), 201–215. https://doi.org/10.1049/wss2.12068
Pitchaipillai, P. (2024). Link Reliable on-Demand Distance Vector Routing for Mobile Ad Hoc Networks. International Journal of Information Technology. https://doi.org/10.1007/s41870-024-01975-y
Rady, A., El‐Rabaie, E. L. M., Shokair, M., & Abdel‐Salam, N. (2021). Comprehensive Survey of Routing Protocols for Mobile Wireless Sensor Networks. International Journal of Communication Systems, 34(15), e4942. https://doi.org/10.1002/dac.4942
Ramamoorthy, R., & Thangavelu, M. (2020). An Improved Distance‐Based Ant Colony Optimization Routing for Vehicular Ad Hoc Networks. International Journal of Communication Systems, 33(14), e4502. https://doi.org/10.1002/dac.4502
Saxena, S., Bhushan, B., & Ahad, M. A. (2021). Blockchain-Based Solutions to Secure IoT: Background, Integration Trends and a Way Forward. Journal of Network and Computer Applications, 181, 103050. https://doi.org/10.1016/j.jnca.2021.103050
Singh, C., & Jain, A. K. (2024). A Comprehensive Survey on DDoS Attacks Detection & Mitigation in SDN-IoT Network. E-Prime – Advances in Electrical Engineering, Electronics and Energy, 8, 100543. https://doi.org/10.1016/j.prime.2024.100543
Taherdoost, H. (2022). What are Different Research Approaches? Comprehensive Review of Qualitative, Quantitative, and Mixed Method Research, their Applications, Types, and Limitations. Journal of Management Science & Engineering Research, 5(1), 53–63. https://doi.org/10.30564/jmser.v5i1.4538
Tournier, J., Lesueur, F., Le Mouël, F., Guyon, L., & Ben-Hassine, H. (2020). A Survey of IoT Protocols and Their Security Issues Through the Lens of A Generic IoT Stack. Internet of Things, 16, 100264. https://doi.org/10.1016/j.iot.2020.100264
Wylde, V., Rawindaran, N., Lawrence, J., Balasubramanian, R., Prakash, E., Jayal, A., Khan, I., Hewage, C., & Platts, J. (2022). Cybersecurity, Data Privacy and Blockchain: A Review. SN Computer Science, 3(2), 1–20. https://doi.org/10.1007/s42979-022-01020-4
Yan, J., & Jin, D. (2015, June). A Virtual Time System for Linux-Container-Based Emulation of Software-Defined Networks. In Proceedings of the 3rd ACM SIGSIM Conference on Principles of Advanced Discrete Simulation (pp. 235–246). https://doi.org/10.1145/2769458.2769480
Yao, H., & Guizani, M. (2023). Intelligent Traffic Control. In Wireless Networks (pp. 111–209). https://doi.org/10.1007/978-3-031-26987-5_4
Zin, S. M., Anuar, N. B., Kiah, M. L. M., & Pathan, A. S. K. (2014). Routing Protocol Design for Secure WSN: Review and Open Research Issues. Journal of Network and Computer Applications, 41, 517–530. https://doi.org/10.1016/j.jnca.2014.02.008
 This work is licensed under a: Creative Commons Attribution 4.0 International License
This work is licensed under a: Creative Commons Attribution 4.0 International License
© Granthaalayah 2014-2025. All Rights Reserved.